The Android multitasking mechanism, as demonstrated recently, can be plagued with app switching attacks, in which a malicious app replaces the legitimate top activity of the focused app with one of its own, thus mounting, e.g., phishing and denial-of-service attacks. Existing market-level defenses are still ineffective, as pure static analysis is fundamentally unable to reason about the intention of an app and pure dynamic analysis has low coverage.
TDroid is a market-level approach for effectively detecting app switching attacks.
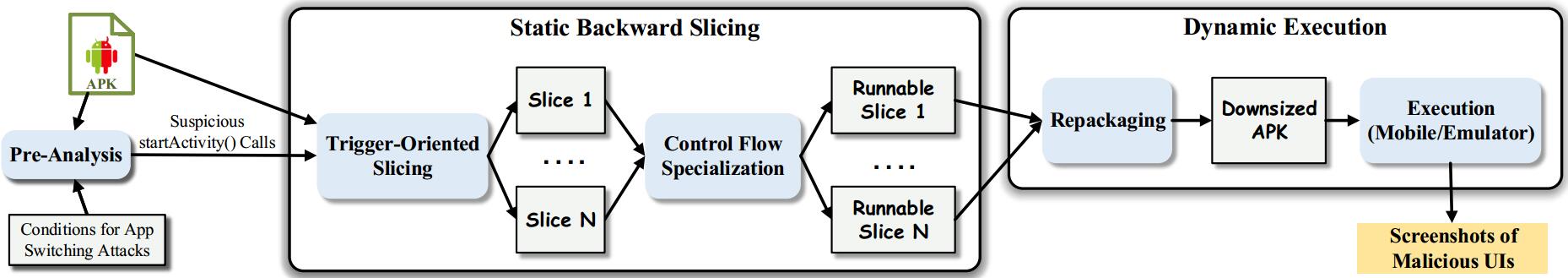
TDroid combines static and dynamic analysis to detect app switching attacks. In its static analysis, TDroid identifies suspicious startActivity() calls leading to such attacks in an app and transforms the app into a number of runnable slices containing potentially app switching attacks, one slice per attack. In its dynamic analysis, TDroid simply executes these runnable slices on an Android device or emulator to expose the malicious calls.

Our subject set consists of a malware dataset and a benign app dataset.
TDroid is available for download from here.
Here is the outline of the directory.
.
+-- flowdroid FlowDroid and Soot.
+-- platforms A collection of all android.jar files for the different platform versions.
+-- TDroid Our approach
+-- run.py A Python script to invoke TDroid.
+-- ApkOutput A folder to save downsized APKs.
+-- log A folder to save log files.
+-- $APP_PATH$.txt A file to save log information.
+-- statistics A folder to save statistic informations.
+-- suspicious_calls.txt A file to save suspicious calls reported by TDroid.
+-- t_analysis_time.txt A file to save analysis time of TDroid.
+-- screenshots A folder to save screenshots obtained by TDroid.
+-- apps A folder containing sample apps.
+-- existingtools A folder containing existing testing tools.
+-- README.html A readme file.
In a terminal, please change your current directory to TDroid_directory and run the Python script to start the analysis.
$ ./run.py -app $APP_PATH$ -d $DEVICE_PORT$ -b $BUILD_TOOLS$
Note: One Android emulator should be running before the execution of TDroid.
usage: run.py [-h] [-app APP_PATH | -file FILE_PATH] [-d DEVICE_PORT] [-b BUILD_TOOLS]
arguments:
-h Print this help message and exit.
-app APP_PATH Path to the APK file.
-file FILE_PATH Path to the file that contains APKs paths to test.
-d DEVICE_PORT Provide the port for the device; it has to be an integer number such as 5554.
-b BUILD_TOOLS Path to build-tools folder in Android sdk.
For instance, for a given apk file SlemBunk.apk (MD5:41c9add2be9f4b04047ab232eb08058f). Running the Python script to start the analysis.
$ ./run.py -app $PATH$/SlemBunk.apk -d 5554 -b /home/user/Android/sdk/build-tools/23.0.2
TDroid generates downsized apk files in ./TDroid/ApkOutput.
The analysis time for the SlemBunk.apk is given in ./TDroid/log/statistics/t_analysis_time.txt as follows:
$PATH$/SlemBunk.apk
pre_analysis_time: 13 seconds
static_analysis_time: 150 seconds
dynamic_analysis_time: 310.16 seconds
total_analysis_time: 460.16 seconds
The suspicious calls in SlemBunk.apk is given in ./TDroid/log/statistics/suspicious_calls.txt as follows:
$PATH$/SlemBunk.apk
12
org.slempo.service.d.run_L48_org.slempo.service.activities.ChangeNumber,
org.slempo.service.d.run_L140_org.slempo.service.activities.PayPal,
org.slempo.service.DialogsStarter.onReceive_L12_org.slempo.service.activities.HTMLDialogs,
org.slempo.service.d.run_L98_org.slempo.service.activities.Nab,
org.slempo.service.d.run_L126_org.slempo.service.activities.StGeorge,
org.slempo.service.MainService.j_L22_org.slempo.service.DeviceAdminChecker,
org.slempo.service.d.run_L181_org.slempo.service.activities.Code,
org.slempo.service.d.run_L22_org.slempo.service.activities.Cards,
org.slempo.service.d.run_L84_org.slempo.service.activities.Commbank,
org.slempo.service.d.run_L67_org.slempo.service.activities.GM,
org.slempo.service.d.run_L112_org.slempo.service.activities.Westpack,
org.slempo.service.d.run_L158_org.slempo.service.activities.CommonHTML
The exposed UIs (screenshots) of suspicious calls in SlemBunk.apk is given in ./TDroid/screenshots/SlemBunk.apk/ as follows:
Please see the details in README.html in the archive.